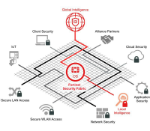
Are Your Point Solutions Creating Vulnerabilities in Your Network?
How Do You Communicate Security Strategy to the C-Suite?
Is Complexity the Enemy of Security?
Fortinet Announces Acquisition of AccelOps
Bayrob - An Ancient Evil Awakens, Are You Prepared for This?
While ransomware has attracted much attention from security researchers lately, other malware hasn't stopped. They are quietly seizing their own place in the attack market. This article analyses one of them - "Bayrob". Our analysis is based on a new variant of Bayrob. We will discuss its background and describe some of its most interesting features, including the purpose of several different processes/services, code obfuscation, data encryption, and its C&C communication. BackgroundThe family of ...
The Couple Soon Discovered that a Stranger had Hacked their Baby Monitor.
What is your plan to protect your entire network from baby monitors to, big data? Her blood ran cold. The couple soon discovered that a stranger had hacked their baby monitor. Late at night, he would take over commands--and even the night-vision lens--to whisper disturbing messages to their toddler. Since CBS 2 in New York reported this story in 2015....
Even a HUGE Wall May Not Be Enough
Q: Why are conventional firewalls no longer enough? A: They never were to begin with. We caught up with Don Kopanoff at HIMSS 2016 to talk about the current state of security - and for him, it's all about the rising complexity of threat...
Is Perimeter-Only Focused Security Obsolete?
Few enterprises can confidently say where their corporate network ends and where their customers, business partners and service providers begin, making perimeter-only focused security obsolete.
Do You Know Who is Controlling Your Thermostat? #IoT Security
Fortinet unveiled a new Security Fabric designed to arm global enterprises with pervasive and adaptive cybersecurity from the IoT to cloud networks. To learn more, visit our website, read our blog posts or download our white paper here.
What tactics have you taken to build a secure foundation to protect your internal networks?
How Do You Help Your Employees Protect their Digital Identity?
The IoT security battle is lost if you're uncertain that the person or thing on the other end of an online transaction is actually who or what it claims to be. Most IoT attacks occur when malicious actors are able to replace an authentic sensor with a compromised device, or when unauthorized remote access is gained and transmits a false signal to a device. To prevent these kinds of attacks, digital identity must establish effective online trust for all connected ...
Who Has Access to Your Lights? Your Automated Plant Feeders? And Your Data?
Market analysts estimate that by 2020 each person will own 26 IP-enabled devices, and over 50 billion IoT devices will come online. Each of these will need to transmit and receive data, run applications, perform transactions, and access services. At...
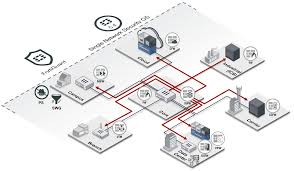
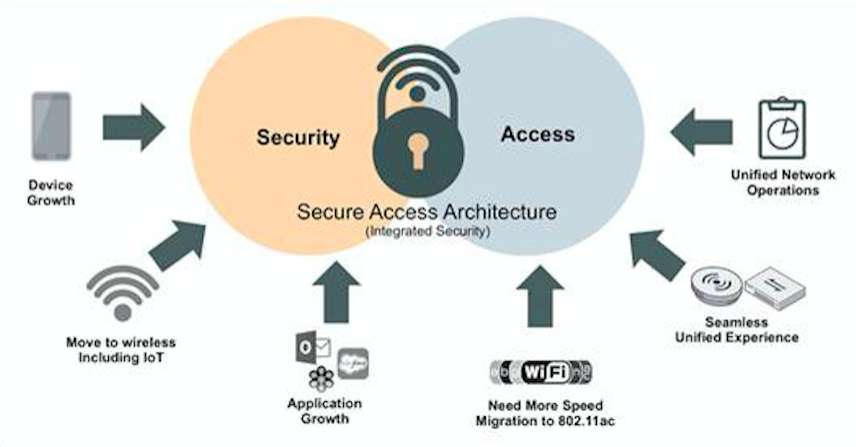
Secure Access Architecture
What are your top security concerns for 2016?
Is the Network Border Dead?
How Does Your Organization Solve the Cybersecurity Skills Shortage?
Executive Perspectives :: Bob Vescio, Verizon and Emily Mossburg, Deloitte - C-Suite TV
Every business is worried about cyber security and how such breaches hinder their daily business operations. Verizon and Deloitte have formed a holistic partnership in order to help keep their customers' data safe. Verizon's Bob Vescio states that more organizations are using 'gut-checking intuition' as a strategy but that alone is not working. ...
How Does Data Inform Your Security Plan?
CryptoWall, TeslaCrypt and Locky: A Statistical Perspective
Rosen Hotels & Resorts discloses data breach
What are Your Top Security Challenges in 2016?
25 CISOs identify the biggest security challenges as they enter 2016. Who do you agree with?